-
Posts
5,964 -
Joined
-
Last visited
-
Days Won
17
Content Type
Profiles
Forums
Downloads
Gallery
Events
Articles
Posts posted by chain
-
-
Facebook released its internally-developed Pysa security tool. Based on the open-source code of Pyre project, Facebook designed Pysa as a static code analyzer. The tool specifically looks for security bugs, unlike most other analyzers. Facebook decided to opensource the tool after witnessing its success in security Instagram. The tech giant’s internal team used the tool for identifying various bugs. Sharing the details of the tool in a post, Facebook stated,
Attribution link: https://latesthackingnews.com/2020/08/11/facebook-launches-pysa-instagram-security-tool-as-open-source/
-
;;;; YOUTUBE DETECTION on $*:Text:/(^[\+-])ytdetect$|(http\x3a\/\/|www\.)(([\S]*youtube\.com[\S]+v\=)|(youtu\.be\/))([\S]{11})/Si:#: { if (!$sock(youtube)) && (!%youtube.flood) { sockopen -e youtube www.youtube.com 443 | sockmark youtube $+(#,>,$replace($nick,>,Guest_),>,$regml(4)) set -eu5 %youtube.flood on } } on $*:Action:/(^[\+-])ytdetect$|(https\x3a\/\/|www\.)(([\S]*youtube\.com[\S]+v\=)|(youtu\.be\/))([\S]{11})/Si:#: { if (!$sock(youtube)) && (!%youtube.flood) { sockopen -e youtube www.youtube.com 443 | sockmark youtube $+(#,>,$replace($nick,>,Guest_),>,$regml(4)) set -eu5 %youtube.flood on } } ;// YouTube Detector Socket (Video Information) // on *:sockopen:youtube: { ;echo -a $+(/watch?v=,$gettok($sock(youtube).mark,3,62)) sockwrite -n $sockname GET $+(/watch?v=,$gettok($sock(youtube).mark,3,62)) HTTP/1.0 sockwrite -n $sockname HOST: $+(www.youtube.com,:,443) $+ $str($crlf,2) } on *:sockread:youtube: { var %x | sockread %x if ($regex(%x,<meta\sname="title"\scontent="(.+)">)) { doecho $gettok($sock(youtube).mark,1,62)) $gettok($sock(youtube).mark,2,62)) $+ : YouTube Info: $replace($striphtml($regml(1)),&,&) sockclose sockname } }
-
One More Chrome Zero-Day Fixed Two weeks after addressing a zero-day, Google disclosed and addressed one more bug in Chrome under active attack. The bug, CVE-2020-16009, caught the attention of Clement Lecigne of Google’s Threat Analysis Group and Samuel Groß of Google Project Zero. As disclosed, the new zero-day bug affects the V8 component of the Chrome browser. Although, Google also fixed another zero-day flaw in the V8 component earlier this year. But that was a type confusion flaw, while for the recent bug, Google has described it as inappropriate implementation. As per their policy, Google hasn’t disclosed any details about the bug yet besides admitting its exploitation in the wild.
-
On *:START: { echo 3 -s *** CONNECTING IN 5 SECONDS. HOLD SHIFT to ABORT. if ($mouse.key & 4) { echo 4 -s *** SHIFT key detected: Auto-connect aborted! | return } .timerSTARTCONNECT 1 5 startconnect } ALIAS startconnect { if ($mouse.key & 4) { echo 4 -s *** SHIFT key detected: Auto-connect aborted! | return } ; server $server -i $mnick $anick $email $fullname -jn #chan1,#chan2,#chan3,etc server efnet +9999 -i Raccoon Raccoon` racc@- I am Raccoon -jn #mIRC,#irchelp,#efnet server -m freenode -i Raccoon Raccoon` racc@- I am Raccoon -jn ##mIRC,#irchelp,#freenode server -m irc.mircscripts.net +6697 -i Raccoon Raccoon` racc@- I am Raccoon -jn #mirc,#chat,#help server -m irc.swiftirc.net +6697 -i Raccoon Raccoon` racc@- I am Raccoon -jn #msl,#help } By: Raccoon -
The free Internet Relay Chat (IRC) network run by the Undernet is continuing to be assaulted by distributed denial-of-service attacks, leading some of the companies that operate the group’s servers to terminate their hosting agreements.
In an updated notice posted Thursday on its Web site, the Undernet’s administrators said it’s still uncertain when they will be able to restore the IRC network to full working order. The networks of the Internet service providers that host Undernet servers in the U.S. and Europe “have been subjected to continued denial-of-service attacks,” the statement said.
Such attacks have been a frequent problem with IRC servers, according to the Undernet advisory. But it added that the attacks being carried out this week “have been so severe that some [companies] have terminated their agreements to host IRC servers on the Undernet network.”
Even disconnecting the IRC servers hasn’t stopped the attacks, the notice said. Hosting companies that have taken that step are still being assaulted, leading the Undernet’s administrators to conclude that the attackers are trying “not only to destroy an IRC network, but also to adversely impact the business enterprise of individual ISPs that have hosted Undernet IRC servers.”
IRC is a real-time text messaging service that predates many of the instant messaging services now available online, such as America Online Inc.’s Instant Messenger. Millions of people use IRC, and Undernet is one of the largest networks, with 45 servers connecting users in more than 35 countries.
But the Undernet’s administrators said the future of the group’s network remains uncertain because of the ongoing attacks, which are believed to be originating from Romania.
An Undernet system administrator who spoke on condition of anonymity said the recent attacks are nothing new for IRC services. However, he said this assault appears to be an act of revenge by someone who was denied access to a specific IRC channel.
Efforts to reach Undernet officials for additional comment today were unsuccessful. The denial-of-service attacks were first reported last Sunday and have forced the organization to shut down most of its free messaging services.
Most Undernet servers are operated by Internet service providers and Web hosting firms. There are 17 Undernet servers in the U.S. and Canada at companies such as America Online Inc., AT&T Worldnet and MindSpring Enterprises Inc. As in other distributed denial-of-service (DDOS) attacks, the servers are being flooded with phony information requests that overload them.
Jim Dreher, vice president of Internet product management at Princeton N.J-based RCN Corp., said the attack has had no impact on commercial operations that are run through its Erols Internet unit. “We haven’t experienced too many problems and don’t have any plans to take [an Undernet server hosted by Erols] down,” he said, adding that the system “is pretty low maintenance.”
Although Dreher said DDOS attacks are “always a problem on IRC,” he noted that the chat technology is a minor service for most ISPs. “It’s really the techie elite that use IRC,” he said.
The other U.S. ISPs that host Undernet servers didn’t respond to requests for comment by deadline.
Darren Reed, a software engineer and consultant at Optimation Software Engineering Ltd. in Melbourne, Australia, who was involved in some of the early IRC software work, said the denial-of-service attacks could add a significant amount of traffic to an ISP’s network.
But for most Internet users, Reed added, the ongoing assaults aren’t a big deal. “Unless you use IRC, I don’t think this is something you should be worried about,” he said.
Rick Forno, a security officer at Network Solutions Inc., a major domain name registrar in Herndon, Va., also said the attack against the Undernet shouldn’t concern the general Internet user population.
“IRC is not used by that many people in the mainstream,” Forno said. The only real impact, he added, is that some ISPs hosting Undernet servers are seeing increased traffic on their networks and Undernet users are suffering degraded IRC service.
But for some of the companies that host Undernet servers, the choice of whether or not to continue doing that could be an easy one, according to Reed.
“Traditionally, IRC has been run at many ISPs and universities as a ‘guest’ [service or] something a staff member has supported for personal reasons,” Reed said. “With no real business case to support it being present, with crippling amounts of data entering networks to attack IRC servers, the choice about whether or not to keep the server isn’t much of a choice at all.”
Undernet administrators made much the same point in the notice posted on the network’s Web site. “While [ISPs] are currently paying for the resources to provide a free IRC environment, they cannot continue to do so if they suffer substantial losses of business revenue,” they warned.
source: https://www.itworldcanada.com/
-
President Donald Trump’s positive COVID-19 result has made Twitter a busy place in the past 24 hours, including some tweets that have publicly wished — some subtly and others more directly — that he die from the disease caused by coronavirus.
Twitter put out a reminder to folks that it doesn’t allow tweets that wish or hope for death or serious bodily harm or fatal disease against anyone. Tweets that violate this policy will need to be removed, Twitter said Friday. However, it also clarified that this does not automatically mean suspension. Several news outlets misreported that users would be suspended automatically. Of course, that doesn’t mean users won’t be suspended.
Motherboard reported that users would be suspended, citing a statement from Twitter. That runs slightly counter to Twitter’s public statement on its own platform.
source: techcrunch.com
-
In Memoriam
From its humble beginnings to the latest release, BitchX has always been about community. Over the years, a handful of people have voluntarily contributed a great deal of time and energy to the project by writing scripts, providing support, troubleshooting, patches, enhancements - or simply making BitchX a fun thing to be involved with. With such a long history, we have had our losses. Several of the friends that we came to regard as a kind of extended family left us before their time, and we would like to remember them here.
ssshooter
Jason Higham, known to his friends on IRC as ssshooter, left us on July 11th, 2004. He is remembered fondly by his family and friends.
sellfone
On the 18th of July, 2004, our dearly missed friend Miles Wilson (also known as sellfone) passed away in his sleep.
turtlex
Amy Elizabeth Haskew died on June 16, 2009 at 34. Goodbye turtlex, you'll always be remembered as someone very kind, and wise beyond your years.
frash
RIP Marc Casillo aka frash [25/Nov/1970 - 28/Sep/2009]
void
Matthew Luberto, known to his many friends online as void, passed away in his sleep on February 16, 2013 in his 38th year. We'll miss you, void.
-
 1
1
-
-
Happy Birthday to my long friend and IRC and website partner Wes. Its been a long and somewhat an experince being your friend and Website and server partner LOL From MSN to Neo_vortex to NSM we have always maintained a great friendship and still continue to do so. all I can say bro is have a great one and many more to come my good friend!!
Your Good Friend Chain
-
UnoBot is an IRC bot that is written in java. It has a pircbotx back end so it's easy to change settings. The bot connects to an IRC server/channel and allows members of the channel to play a game of uno. It also has an AI so it can play too.
Requirements
- You must have Java 1.7 JDK or higher installed.
- The Java bin folder must be in your classpath if you are running windows.
- Maven
Installation
- open the config.ini file
- edit the values appropriately
-
run
mvn package(you will have to cd to UnoBot's directory) -
run
UnoBot-1.0-SNAPSHOT-jar-with-dependencies.jarusing thejava -jar ./target/UnoBot-1.0-SNAPSHOT-jar-with-dependencies.jarcommand
-
Ive used this client for a long time but im finding the developers are not really doing much too it as they use too. its a great client but you have a certain amount of plugins to use and none updated, same with the theme section. Its not like mIRC where you can do things with it as this client is a c++ which is complicated unless ur in that field range. its still a good client and has many options but slowly getting more and more limited.
resource page: https://www.kvirc.net/ -
Ive been using a old client thats developers continue to update. AdiIRC is still a pretty good client has many features and themes to it. if interested heres the resource page
-
We have now also opened a facebook for coder-irc & coders-resources. We will make sure that any network updates and changes will be plublished on here & our site for continous updates on all website and server detail go to facebook or server website or resource website.
-
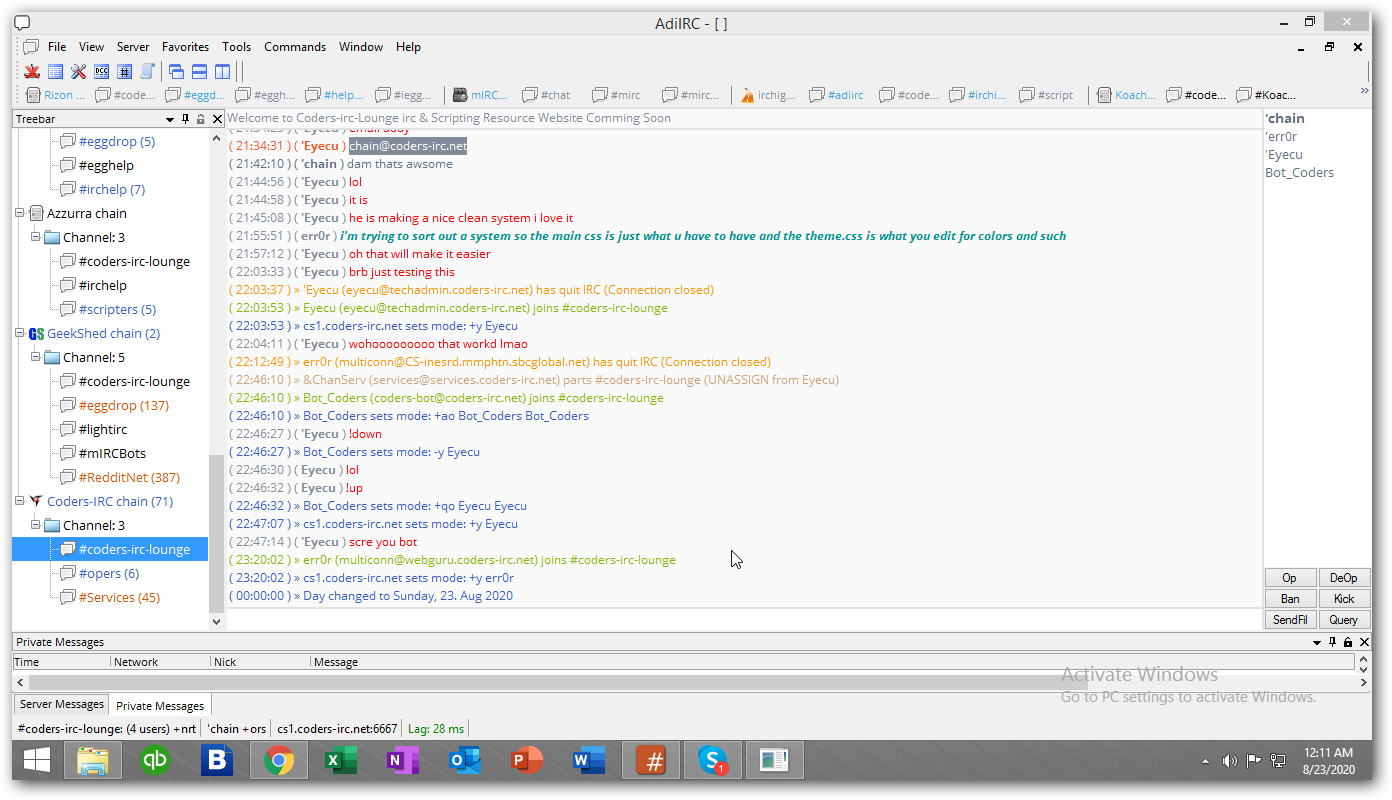
We have squired now new server addresses which are now
Connection infocs1.coders-irc.net 6667 non-ssl<----Newark,NJ USAcs1.coders-irc.net 6697 ssl<----Newark,NJ USAcs3.coders-irc.net 6667 non-ssl <----london englandcs3-coders-irc.net 6697 ssl <-----London Englandirc.coders-irc.net is the round robin -
Welcome to coders-resources website this website is mainly for IRC resources and for coders.



Best Dubstep Mix 2020 [Brutal Dubstep Drops]
in Coders-Resources News
Posted
http://bit.ly/1bhqmrm